application lifecycle management (ALM)
What is application lifecycle management?
Application lifecycle management (ALM) is an integrated system of people, tools and processes that supervise a software application from its initial planning and development, through testing and maintenance, and into decommissioning and retirement. By combining and organizing the elements of an application's lifecycle, ALM improves product quality, optimizes productivity and eases the management and maintenance burden for related products and services.
ALM tools automate software development and deployment processes, help ensure that compliance is achieved and maintained, and create a standardized environment where all teams involved in the application lifecycle can communicate and collaborate.
Why is ALM important?
ALM helps companies set and meet appropriate requirements for projects. ALM also improves the development process by incorporating frequent, thorough testing. It also helps developers adjust development processes and goals during the software lifecycle. Finally, ALM helps ensure that all teams -- including development, operations and security -- can collaborate effectively to produce the best possible software.
Furthermore, leading software companies deploy updates for products daily. Application lifecycle management helps businesses achieve high efficiency and gain a competitive edge by accelerating workflows and ensuring that top-quality products get deployed.
This article is part of
What is desktop management and how does it work?
What is ALM used for?
ALM provides a framework for setting requirements and establishing processes, governance and methodologies before deploying software. Thus, ALM supplies the scaffolding within which software gets developed, tested and maintained. By design, it also includes safeguards and checkoffs to ensure that software meets compliance, governance, efficiency, usability, performance and other benchmarks before being released into production. Finally, ALM provides ongoing opportunities to review and adjust costs to meet changing budget requirements and productivity assessments to ensure that companies realize their ROI objectives for software development.
What is the ALM process?
The ALM process gives DevSecOps teams, plus executive staff and stakeholders, ongoing opportunities to:
- set and manage requirements and establish processes and procedures;
- set and manage governance and compliance needs across the lifecycle;
- establish methodologies to manage and control development, testing and maintenance activities; and
- ensure that testing meets functionality, performance, usability and security needs.
As explained in the next section, the ALM process makes sure that all aspects for all stages of application lifecycle management are explicitly established and managed.
Stages of ALM
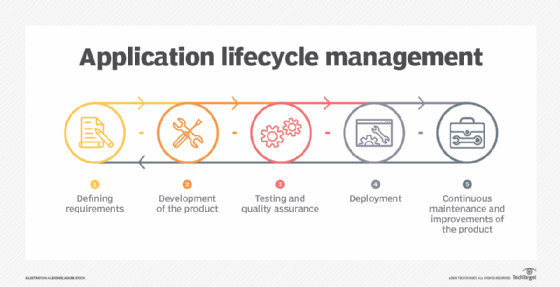
Application lifecycle management consists of five stages:
- Defining requirements
- Development of the product
- Testing and quality assurance
- Deployment
- Continuous maintenance and improvement of the product
1. Defining requirements
When defining requirements, all stakeholders gather to declare what they need from the application to support their business cases. A design of the application is created based on their expressed needs. Requirements can include a range of factors, from the business needs of the stakeholders to compliance and governance requirements.
Specifying requirements usually happens top-down, meaning the needs start with the most general and move into the more specific and detailed. As a result, case requirements are often in a hierarchical tree structure, with each node representing a more specific sub-requirement for a more general parent node. However, other development approaches, such as the iterative Agile development process, use less hierarchical structures to list requirements, with the defined needs identified as use cases.
2. Development of the product
Development of the product begins once the team agrees on the requirements. The product moves from an idea and design to a real, working application in this stage. At the start, the development team must break down the application requirements into pieces and phases to create a development plan.
It is beneficial to incorporate representatives from all related teams during this time, including sales, product marketing, IT and testing. This helps ensure that the created product satisfies all defined needs and is easy to use, test and deploy.
A wide variety of development methodologies can happen during this stage. The most popular are sequential -- for example, the Waterfall model -- or iterative -- such as Agile development.
3. Testing and quality assurance
Testing and quality assurance often overlap with the development stage. Testers should begin preparing their test cases and testing environments before the product is formally released. Testers should also be available to provide feedback on the application throughout development. Furthermore, integration and unit tests should be incorporated into programming activities. Development teams often use continuous integration systems.
During the formal testing and quality assurance stage, testers must verify that the application fulfills the requirements defined in the first stage of the process. Testers should also check for all other stakeholder expectations that the app will need to support throughout its lifecycle. This stage also includes full integration testing, and all issues or bugs discovered and reported may be addressed by the development team.
The development and testing stages conclude when the product reaches quality and stability good enough for release. The product marketing team defines this level.
4. Deployment
The deployment stage involves the release of the product to users. This process varies based on the application type because each product type requires different attributes and specifications. For example, software as a service (SaaS) apps must be deployed on the company's internal servers, while users can access web apps through the internet.
5. Continuous maintenance and improvement of the product
Continuous maintenance and improvement of the product occur after deployment to monitor and manage the performance of the released application. During this stage, the team resolves any remaining bugs while planning and prioritizing new updates.
Maintenance is frequently the longest stage of application lifecycle management, but it can also require the least participation from the development team if previous steps were effective.
An important element of the maintenance stage is defining the system's retirement. In other words, teams must decide on the point at which work should be stopped and moved to a newer version of the product or migrated to a different product entirely.
Benefits of application lifecycle management
Some key benefits of ALM include:
- Increased visibility into workflow
- Enhanced compliance
- Faster deployments
- Higher-quality products
The integrated system created by ALM is more efficient than a collection of unconnected tools and processes spread across various teams. This integration also benefits organizations by improving communication and collaboration and aligning software objectives with any business value or corporate goal.
The ability for teams to collaborate ensures that each worker understands the project and its stage. ALM tools allow workers to track strategies, changes, requirements and project status in real time, regardless of their location. ALM tools also prioritize the various team goals and help define the various skill sets needed for different processes.
In addition, application lifecycle management provides an organization with a clear direction for its workflow before developers begin building the app. The first stage -- defining requirements -- allows companies to develop a business case, determine the app's lifespan and plan the necessary resources before committing to development. This saves the organization time and money by avoiding unnecessary work and expensive mistakes.
ALM also improves teams' decision-making abilities when dealing with aging software. Most ALM tools include version control and real-time planning, allowing team leaders to easily map the application's future. This capability can also eliminate confusion for companies dealing with multiple applications.
ALM tools
A collection of project management tools that integrate people and processes, called application lifecycle management tools, enables ALM. Numerous ALM tools are available for tracking application changes.
These tools range from dedicated ALM products that monitor an application from inception to completion, automatically sorting files into logical buckets, to simple wikis that require team members to record changes manually.
Organizations should look for several key features when choosing an ALM tool:
- version control;
- team communication and planning in real time;
- estimation and planning;
- requirements management;
- test management and quality assurance;
- source code management;
- automated deployment;
- application portfolio management; and
- maintenance and support.
The ALM tool allows users to define project requirements and develop user stories, which can then be prioritized, scheduled and broken down into detailed tasks used for resource tracking. Resource tracking analyzes how well an organization uses its resources throughout the app's lifecycle. ALM tool users can also attach documents, screenshots and URLs to all artifacts and customize all graphs and reports in various formats -- including Adobe Acrobat and HTML.
ALM tools enable users to create, modify and perform test cases; manage automated and manual tests; track issues, bugs, risks and enhancements related to the source code repository; and access a complete audit history of all changes made to the application. ALM tool dashboards can be personalized, and the reporting that appears can be customized to best benefit the specific user.
Some popular examples of ALM tools include the following:
- Jama Software
- MeisterTask
- Codebeamer
- Visure
- Jira
- Microsoft Azure DevOps
- Tuleap
ALM vs. SDLC
Software development lifecycle (SDLC) refers to the processes or procedures involved in creating a high-quality software product. Application lifecycle management is similar to SDLC, but it incorporates a larger range of processes.
While ALM covers the entire application lifecycle, SDLC only focuses on the software development process. In other words, ALM includes all five stages of the app's lifecycle -- requirements, development, testing, deployment and maintenance -- but SDLC only includes one stage -- development.
Consequently, application lifecycle management includes software development lifecycle, but SDLC only focuses on a fraction of ALM.







