
Fotolia
Complete guide to penetration testing best practices
Pen testing uncovers security vulnerabilities before hackers do. Use this guide to learn about the tooling options, test types, use cases and common flaws in software penetration testing.
Security posture is a crucial aspect of software design and implementation. Through comprehensive application security testing, IT organizations identify risks, threats and vulnerabilities that malicious actors can exploit.
Software penetration testing, also called pen testing, discovers flaws, and examines the possible consequences of those defects. The organization can then handle those exploits in a safe, controlled and well-documented manner. Although penetration tests also cover the operation of networks, servers and other hardware, developers and testers bear responsibility for weaknesses at the software level.
Ideally, the software's design and codebase allow only authorized users access to features and data stores. In practice, however, software comes with a wide range of risks that might leave the application vulnerable. Unauthorized individuals seek out these weaknesses to gain control of the application and access, alter or steal data.
Get to know common software penetration best practices, including the basics of execution and flaws it can find. You should also understand testing types and tools necessary for the job. This guide covers how teams should approach pen testing and the kinds of software projects that need the security measure most.
Penetration testing best practices
Pen testing basics. Software penetration testing is all about discovery. First, collect information from the available sources to enable penetration tests, then perform a range of tests to find flaws in target software.
It's a best practice to document this work carefully, including the means pen testers use to obtain information, the actual steps and processes they use to test, and the observed results. This way, developers can reproduce flaws later to study and remediate them. Organizations typically conduct penetration testing over a defined time period.
Ultimately, penetration testing requires a team's security professionals to think and act like real hackers, while behaving in a manner that supports business interests -- i.e., to be ethical hackers. Confidentiality is crucial.
Penetration testing use cases. Penetration testing is valuable for all types of security evaluations, but a full-scale effort might not always be worth the work and expense. A simple software module with limited access to data storage, for instance, won't require a multi-team security assessment. Low- or no-code applications enterprises use for internal business tasks are also low priority.
Some software development projects, however, require thorough penetration testing. A retail or financial services company should demand comprehensive, full-scale penetration testing for software involved with monetary transactions, customer data and financial holdings. Similarly, software in certain data- and security-sensitive sectors, including military and healthcare, typically receives detailed penetration testing to find and remediate flaws that might cost lives. Penetration testing can also validate software components external programmers develop.
Finally, an organization can use penetration testing after a security breach. Forensic pen testing provides insight into the flaw that led to the exploit. Developers can then search for additional flaws in the code and its supporting infrastructure hackers have yet to exploit.
Identifiable application security risks. Countless flaws can put an application at risk and threaten information security. Pen testers commonly find flaws in:
- the OS
- application code
- configuration files
Applications rely heavily on the OS for resources, including the UI, storage access and a network interface. OS weaknesses can potentially give a malicious actor control of application behavior or inappropriate access to storage. Consider how an OS manages ports for communication to and from the network. A hacker can use port scanning to detect open ports to attack the system and software. Install all OS security patches to protect applications and data.
Development oversights and unintended flaws in application code can disrupt productivity, expose data and even crash the software. If a team overlooks error handling, for example, an application won't deal smoothly with disallowed inputs. Also, developers might hard-code default login credentials into the software and never remove them before the code goes live. Or, developers might enable an application to save and access some files without restricting customer access; this a failure to anticipate certain user actions.
Software configuration files often detail important variables, such as default data storage directories and network communication information. Attackers look for configuration files to identify avenues of attack -- or even use their information to make software changes that open the door for an intrusion. Protect configuration files against snooping and set up a process to authorize any changes.
Penetration testing drawbacks
While a valuable approach for the business and IT, penetration testing isn't perfect.
First, penetration testing guarantees nothing. The test approach only succeeds when a flaw is found and fixed. You can miss flaws, only to have them discovered later.
Second, penetration testing consumes considerable time and staff resources. Weigh the benefits against the project budget. Budget can restrict how much penetration testing a team performs on a build. Sensitive projects with significant penetration testing requirements can get pricey.
Penetration testing can result in unexpected downtime and data loss or corruption -- side effects of exploited flaws in software. Mitigate these problems through A/B testing, in which an older build continues to run while the new build undergoes software testing and validation. Data protection methods, such as backups and snapshots, also help guard against unexpected data loss.
Software penetration testing types
A hacker's knowledge about the system or software they're attacking can vary dramatically. Through penetration testing, organizations can mimic everything from a hacker with no awareness of an application's security controls to one with knowledge of every security measure. Consider these types of penetration testing.
Black box penetration testing. In a black box scenario, hackers have virtually no information about the system or software they attack. There is no insight into the server hardware, the network, the storage configuration or the software application that runs on the infrastructure. This scenario means the target is a black box -- an unknown entity.
Penetration testers, like their malicious hacking counterparts, typically rely on a trial-and-error approach to finding common flaws and vulnerabilities. As part of a black box approach, a pen tester might attempt to gain administrative access to a system using common default administrator credentials.
Of all the types of software penetration testing methods, manual black box attempts take the longest to complete and offer the lowest chance of success. Penetration testers usually rely on automated tools that run through common flaws and vulnerabilities.
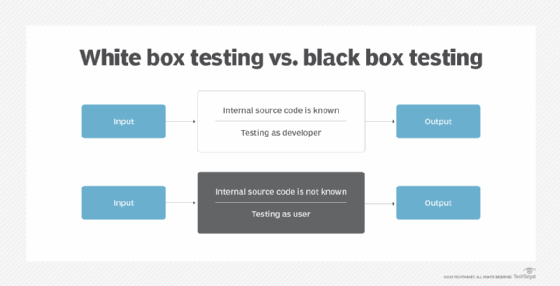
White box penetration testing. In a white box approach, a penetration testing team has access to all information about the system or software under test. Information can include the software's source code, as well as server and network architecture diagrams.
Unlike real-life attackers, white box penetration testers have almost perfect insight into the system, which aids their search for flaws and vulnerabilities. More information means specific manual penetration tests that speed up the testing process and enable smaller testing windows. However, it's difficult to find the weakest or most vulnerable flaw when you have all the information. Rather than identify the most discoverable flaw, these pen testers might find ones obscured to most hackers, which the latter are unlikely to target.
Gray box penetration testing. The gray box testing approach provides a penetration testing team with incomplete or partial knowledge of the system or software under test. Gray box pen testers might get the source code or the system configuration details, but perhaps not both.
This partial information leads to mixed testing tactics. Penetration testers usually focus their simulated attacks first on the known information and then systematically expand the attacks to try for vulnerabilities and flaws where less is known.
How to perform penetration testing
Now that you know the best practices around when to use software penetration testing, learn how to execute these ethical hacks. Pen testing is rarely a solo activity. Larger software projects might engage several competing teams in a testing exercise. For example, a hacking team performs penetration testing, while a team of IT security staff identifies and responds to their attacks.
Organized penetration testing efforts typically follow a four-step process that includes:
- planning
- discovery
- attack
- reporting
The penetration testing lifecycle might repeat for each build, or simply when a different perspective is required, such as white box rather than black box testing.
Planning. Penetration testing costs money, so every test cycle needs a business justification. Penetration test planning defines the scope, approach, goals and limitations of the project. Imagine how a development team will perform pen testing on a pre-release build to ensure that it adheres to existing security policies and also satisfies compliance needs.
Discovery. In this phase, penetration testers collect and assess as much information as possible about the software and its related systems. Scan for open ports, check for vulnerabilities and use social engineering to collect usernames and passwords. The discovery phase is most important in black box testing, where testers don't have much intelligence to start with.
Attack. This limited-duration phase is when a penetration testing team uses information it discovers to validate and exploit flaws in the software. The goal is to mimic the actions of a potential hacker or malicious user. Pen testers attempt to access resources, functionality and data. Although penetration testing is not intentionally malicious, the attack can result in undesirable consequences, such as software disruption and data loss. This possibility is a necessary risk.
Reporting. Penetration testing generates feedback for a development team and other stakeholders of the software. Reporting is a vital conclusion to the penetration testing cycle. Reporting renders detailed findings:
- the intelligence uncovered;
- vulnerabilities and flaws discovered;
- exploits validated; and
- detailed remediation recommendations.
Software penetration testing tools
Penetration testing encompasses a wide array of techniques, such as web app hacking and SQL injection. There are dozens of vulnerability and penetration testing tools and services, including:
Product suites
- Burp Suite, PortSwigger tools that can scan web apps for vulnerabilities, and map content and functionality; and
- Indusface, a product line that provides web app scanning and a firewall, plus digital SSL certificates and mobile security testing.
Network and vulnerability scanners
- Acunetix, an end-to-end web vulnerability scanner;
- Intruder, a cloud-based vulnerability scanner;
- Nessus, a commercial vulnerability scanning product;
- Netsparker, based on an automated security vulnerability scanner;
- Nmap, a free open source network and port scanner;
- Wireshark, an open source network protocol analyzer; and
- Zed Attack Proxy, an Open Web Application Security Project tool that provides free vulnerability scanning for web apps.
SQL injection
- sqlmap, an open source tool that automates SQL injection; and
- sqlninja, a tool for exploiting SQL injection for apps that use Microsoft SQL Server.
Password security
- Cain and Abel, a password recovery and cracking tool; and
- John the Ripper, a password cracking tool.
Cybersecurity search engine
- Spyse, a cybersecurity search engine that provides details on web components.
Frameworks
- Browser Exploitation Framework Project, also called BeEF, an open source tool that focuses on web browsers;
- Core Impact, a commercial penetration testing framework;
- Metasploit, an open source penetration testing framework -- Rapid7 makes a commercial version; and
- w3af, an open source security vulnerability scanner and exploitation tool for web apps.







